In the ever-evolving world of cybersecurity, traditional passwords are increasingly seen as a weak link. Enter passkeys — a modern, passwordless authentication method that’s gaining traction as a more secure and user-friendly alternative. But what exactly are passkeys, and how can they be integrated into IAM (Identity and Access Management) systems? Let’s break it down.
What Are Passkeys?
A passkey is a cryptographic credential that replaces a traditional password. Built on the FIDO2/WebAuthn standard, a passkey uses public key cryptography to authenticate users without transmitting sensitive secrets. It consists of two parts: a public key, which is stored on the service (like a website or app), and a private key, which is stored securely on the user’s device.
The authentication process works like this: when a user attempts to log in, the server sends a challenge that the user’s device signs using the private key. Since the private key never leaves the device, it can’t be stolen in a data breach or phishing attack.
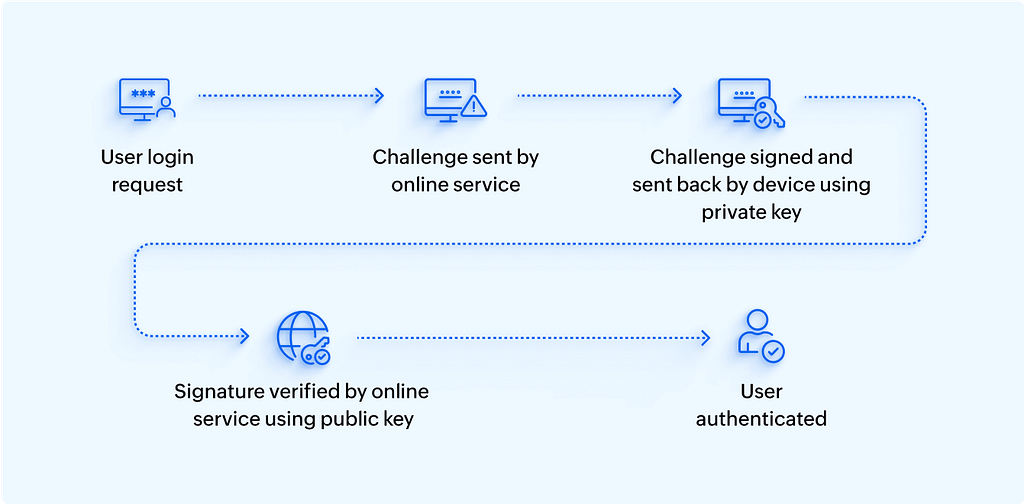
Passkeys can be stored in secure hardware like the TPM (Trusted Platform Module) or the device’s secure enclave, and are typically synced across devices using encrypted cloud storage (like iCloud Keychain or Google Password Manager).
Why Use Passkeys in IAM?
IAM solutions are responsible for managing user identities and their access to resources. Incorporating passkeys into an IAM strategy offers several advantages:
- Phishing resistance: Passkeys can’t be tricked into authenticating a malicious site.
- No password reuse or leakage: Users don’t need to remember or reuse passwords.
- Streamlined UX: Faster and easier logins using biometrics or device PINs.
- Lower support costs: Fewer password reset requests mean reduced helpdesk load.
For businesses, this improves both security posture and user experience, a rare win-win in the cybersecurity world.
Integrating Passkeys Into IAM Solutions
Here’s how passkeys can be implemented within an IAM framework:
- Adopt FIDO2/WebAuthn Support: Ensure your IAM provider or platform supports WebAuthn, the key browser-based API for passkeys. Many modern IAM platforms (like Okta, Azure AD, and ForgeRock) already include this.
- Enable User Enrollment: Allow users to register a passkey during account setup or login. This typically involves biometric verification (like Face ID or fingerprint) or a PIN.
- Multi-Device Sync: Ensure passkeys are synced securely across devices, leveraging platform-specific solutions (e.g., Apple’s iCloud, Google’s ecosystem, or Microsoft Passport).
- Fallback Options: Offer secure recovery options for lost devices — this may include additional authentication methods or re-verification through admin workflows.
- Monitor & Enforce Policies: IAM administrators should monitor passkey usage and enforce MFA policies where necessary, possibly using risk-based access controls.
Final Thoughts
Passkeys represent a significant shift in how we think about authentication — from something you know (passwords) to something you have and are (your device and biometric identity). As phishing threats grow more sophisticated, passkeys offer a compelling path toward a safer, passwordless future. Integrating them into your IAM solution today puts you ahead of the curve in protecting both users and sensitive enterprise assets.
